Friday, 1 July 2011
Thursday, 30 June 2011
Flashback : Understanding the Internet Reference Model
Network Access Layer
The lowest layer. Contains protocols that the computer uses to deliver data to the others computer and devices that are attached to the network. The protocols at this layer perform three distinct function:
Responsible for routing messages through internetwork
Two types of device are responsible:
Responsible for providing end-to-end data integrity and provides a high reliable communication service for entities that want to carry out an extended two way conversation.
Application Layer
The top layer. Provide functions for users or their programs and it is highly specific to the application being perform. It provides the service that user applications use to communicate over the network. It is the layer in which user-access network processes reside.
The layer includes all applications protocols that use the host-to-host transport protocols to deliver data. Others function that process user data such as data encryption and decryption, compression and decompression
The application layer also manages the sessions (connections ) between cooperating applications. TCP/IP uses the term "socket" and "port " to describe the path ("virtual circuit") over which cooperating applications communicate.
For cooperating applications to be able exchange data, they must agree about how data is represented. The application layer is responsible for standardizing the presentation of data.
The lowest layer. Contains protocols that the computer uses to deliver data to the others computer and devices that are attached to the network. The protocols at this layer perform three distinct function:
- Define how to use the network to transmit a frame, which is the data unit passed across the physical connection
- Exchange data between computer and physical network
- Deliver data between two devices on the same network. To deliver data on the local network, the network access layer use the physical address of the nodes on the network.
Responsible for routing messages through internetwork
Two types of device are responsible:
- Gateway - Computer that has two network adapter card. This computer accepts network packet from one network on one network card and routes those packet to a different network via the second network adapter card.
- Router - A dedicated hardware device that passes packets from one network to a different network.
Responsible for providing end-to-end data integrity and provides a high reliable communication service for entities that want to carry out an extended two way conversation.
Application Layer
The top layer. Provide functions for users or their programs and it is highly specific to the application being perform. It provides the service that user applications use to communicate over the network. It is the layer in which user-access network processes reside.
The layer includes all applications protocols that use the host-to-host transport protocols to deliver data. Others function that process user data such as data encryption and decryption, compression and decompression
The application layer also manages the sessions (connections ) between cooperating applications. TCP/IP uses the term "socket" and "port " to describe the path ("virtual circuit") over which cooperating applications communicate.
For cooperating applications to be able exchange data, they must agree about how data is represented. The application layer is responsible for standardizing the presentation of data.
Flashback : TCP/IP
Generally , TCP/IP is described using three to five functional layers.
At the remote end, the data is passed up the stack to the receiving application
Each layer in the stack adds control information (such as destination address, routing control and checksum) to ensure proper delivery.
The control information is called header and/or trailer because it is placed in front of or behind the data to be transmitted. Each layer treats all of the information that it receives from layer above it as data, and it places its own header and/or trailer.
When data is received, the opposite happen, each layer strips off its header and/or trailer before passing the data up to the layer above.
This model is based on the three layer. These three layers are as follows:
- Network access layer
- Host-to-host transport layer
- Application layer
How a Protocol Stack Work
Data is passed down the stack from one layer to the next, until it is transmitted over the network by network access layer protocolsAt the remote end, the data is passed up the stack to the receiving application
Each layer in the stack adds control information (such as destination address, routing control and checksum) to ensure proper delivery.
The control information is called header and/or trailer because it is placed in front of or behind the data to be transmitted. Each layer treats all of the information that it receives from layer above it as data, and it places its own header and/or trailer.
When data is received, the opposite happen, each layer strips off its header and/or trailer before passing the data up to the layer above.
Wednesday, 29 June 2011
Sunday, 26 June 2011
Friday, 24 June 2011
IP Address Table
2^7 | 2^6 | 2^5 | 2^4 | 2^3 | 2^2 | 2^1 | 2^0 |
/17 | /18 | /19 | /20 | /21 | /22 | /23 | /24 |
128 | 192 | 224 | 240 | 248 | 252 | 254 | 255 |
128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
2^7 | 2^6 | 2^5 | 2^4 | 2^3 | 2^2 | 2^1 | 2^0 |
/25 | /26 | /27 | /28 | /29 | /30 | /31 | /32 |
128 | 192 | 224 | 240 | 248 | 252 | 254 | 255 |
128 | 64 | 32 | 16 | 8 | 4 | 2 | 1 |
How to Find Network ID and Host ID
To find Network ID and Host ID
192.168.100.1/31
Default subnet = /24 there 24 bits 1
= 11111111 11111111 11111111 00000000
= 255.255.255.0
There 31 bits 1 in subnet mask = 11111111 11111111 1111111 11111110
decimal = 255.255.255.254
To find Network ID = Count bit 1 in the octet that there is not in the default subnet octet
111111111 11111111 11111111 11111110
2^7 = 128 network
To find Host ID = Count bit 0
2^1 = 2 host
192.168.100.1/31
Default subnet = /24 there 24 bits 1
= 11111111 11111111 11111111 00000000
= 255.255.255.0
There 31 bits 1 in subnet mask = 11111111 11111111 1111111 11111110
decimal = 255.255.255.254
To find Network ID = Count bit 1 in the octet that there is not in the default subnet octet
111111111 11111111 11111111 11111110
2^7 = 128 network
To find Host ID = Count bit 0
2^1 = 2 host
How to Find Network Address
To find Network address
IP Address
AND
Subnet Mask
Network Address
IP address = 192.168.100.0
Subnet Mask = 255.255.255.0
192.168.100.0 (decimal) ---> 11000000 10101000 01100100 00000000 (binary)
255.255.255.0 (decimal) ---> 11111111 1111111 1111111 000000 (binary)
11000000 10101000 01100100 00000000
AND 11111111 11111111 11111111 00000000
11000000 10101000 01100100 00000000
110000000 10101000 01100100 0000000 = 192.168.100.0
IP Address
AND
Subnet Mask
Network Address
IP address = 192.168.100.0
Subnet Mask = 255.255.255.0
192.168.100.0 (decimal) ---> 11000000 10101000 01100100 00000000 (binary)
255.255.255.0 (decimal) ---> 11111111 1111111 1111111 000000 (binary)
11000000 10101000 01100100 00000000
AND 11111111 11111111 11111111 00000000
11000000 10101000 01100100 00000000
110000000 10101000 01100100 0000000 = 192.168.100.0
Thursday, 23 June 2011
Subnet Network
Class | Default Subnet | Network ID | Host ID | CIDR |
A | 255.0.0.0 | w | x.y.z | /8 |
B | 255.255.0.0 | w.x | y.z | /16 |
C | 255.255.255.0 | w.x.y | z | /24 |
Tuesday, 21 June 2011
IPV6
In the coming year, as an increasing number of cell phones, PDAs, and other electronic consumer expand their networking capability, the IPV4 address space will likely run out.
IPV6 addresses are 16 bytes (128 bits).
IPV6 addresses are generally written in the following form:
HHHH:HHHH:HHHH:HHHH:HHHH:HHHH:HHHH:HHHH
In the full notation, pair of IPV6 bytes are separated by a colon and each bytes in turns is represented as a pair of hexadecimal number like in the following example:
E3D7:0000:0000: 88F4: 6F3E:712A:9871
IPV6 addresses are 16 bytes (128 bits).
IPV6 addresses are generally written in the following form:
HHHH:HHHH:HHHH:HHHH:HHHH:HHHH:HHHH:HHHH
In the full notation, pair of IPV6 bytes are separated by a colon and each bytes in turns is represented as a pair of hexadecimal number like in the following example:
E3D7:0000:0000: 88F4: 6F3E:712A:9871
IPV4
An IPV4 is consisting of four bytes (32 bits). These bytes also known as octet.
For readability purposes, human typically work with IP addresses in notation called dotted decimal. IP address that computer see as:
00001010 00000000 00000000 00000001
Is written dotted decimal as:
10.0.0.1
For readability purposes, human typically work with IP addresses in notation called dotted decimal. IP address that computer see as:
00001010 00000000 00000000 00000001
Is written dotted decimal as:
10.0.0.1
IP Address
IP addresses are broken into 4 octet (IPV4) separated by dotted decimal notation.An octet is a byte consisting of 8 bits. There are two parts of an IP address:
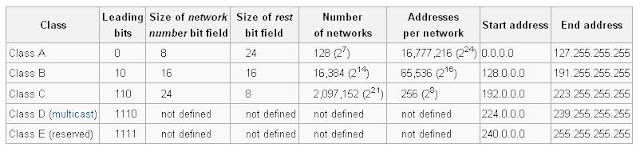
The addressing scheme for class A through E network is shown below.
There are some network addresses reserved for private use. There are three sets of addresses reserved:
- Network ID
- Host ID
The various classes of networks specify additional and fewer octet to designate the network ID versus host ID
Class A-E NetworksThe addressing scheme for class A through E network is shown below.
There are some network addresses reserved for private use. There are three sets of addresses reserved:
- 10.x.x.x
- 172.16.x.x. - 172.31.x.x
- 192.168.x.x
- 127.0.0.1 - The loopback interface address. All 127.x.x.x address are used by the loopback interface
- 0.0.0.0 - Thi is reserved for host that do not know their address and and use BOOTP or DHCP protocols to determine their addresses
- 255 - The value of 255 is never used as an address for any part of IP address. It is reserved for broadcasting address .
Thursday, 16 June 2011
Basic Data Communication
Component data communication
- Sender
- Receiver
- Protocol
- Medium
- Message
- Equipment
 |
| Component of data communication |
Types of Message:
- Text
- Video
- Audio
- Image
- Etc ...
Examples of medium:
- Unshielded Twisted Pair (UTP).
- Shielded Twisted Pair (STP)
- Fiber Optic
- Bluetooth
- Infrared
- Wireless
- Etc..
Equipment consists of:
- Computer
- Bridge - Device filters data traffic, reduce the amount of traffics on a LAN by dividing into 2 segments.
- Router - A device that forwards data packets along network, perform the data "traffic directing" functions.
- Hub - Commonly used to connect segments on LAN, serves simply as a conduit for the data, enabling data to go from one device (or segment) to another.
- Switch - Device that filters and forwards packets between LAN segments.
- Modem - Modulate outgoing digital signals from a computer or other digital device to analog signals for a conventional cooper twisted pair telephone line and demodulates the incoming analog-signal and converts its to a digital signal for the digital device.
Switch VS Hub
Hub
Pass on traffic to network regardless of the intended destination; the PCs which the packets are sent use the address information in each packet to work out which packets are meant for them.
Switch
Control the flow of the network traffics based on the address information in each packet. A switch learns which devices are connected to its network and forwards on packets to the appropriate port only.
Switch VS Bridge
Bridge
Has only two ports and divides a collision domain into two parts. All decisions made by a bridge based on MAC or layer 2 address addressing. A bridge will create more collision domain.
Switch
A fast multi-port bridge. Rather than creating two collision domains, each port creates its own collision domain.
Subscribe to:
Comments (Atom)